Backofficer Friendly Free
Posted By admin On 16.09.19There are tools such as BackOfficer Friendly, available free from NFR Security Inc., which will monitor your system and alert you when an attempt is made to install backdoor software. This program.
Friendly鈥檚, Delivered!
- To fill that void, Network Flight Record, Inc., headed by Marcus Ranum, has introduced BackOfficer Friendly, a spoofing server service that can tell a company when the corporate network's ports have been scanned by an outsider.
- Friendly's has been a favorite family restaurant and ice cream purveyor for over 80 years! Get to know us!
Now you can bring your Friendly鈥檚 favorites right to your door! Order with DoorDash at participating locations today!
Click. Order. Eat!
Create an account to save 50% off your first order. Use the code LOVE50OFF to start your order now.
25% Off Your Next Visit!
Join the BFF Club to get first dibs on exclusive perks including weekly coupons, free birthday sundaes and 25% off your next visit!
Menu
How you like them avocados?
Introducing the new Avocado Turkey Wrap, California Avocado Cobb Salad, and Avocado Chicken Sandwich. Try them all today.
At Your Grocery Store
Make any day even sweeter with your favorite ice cream cartons, cakes and more!
Q: 1
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.weare-secure.com. He wants to test the response of a DDoS attack on the we-aresecure server. To accomplish this, he takes the following steps:
l Instead of directly attacking the target computer, he first identifies a less secure network named Infosecure that contains a network of 100 computers.
l He breaks this less secure network and takes control of all its computers. After completing this step, he installs a DDoS attack tool on each computer of the Infosecure network.
l Finally, he uses all the computers of the less secure network to carry out the DDoS attack on the we-are-secure server.
Which of the following tools can John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
A. Stacheldraht
B. Trin00
C. TFN
D. BackOfficer Friendly
Answer: A, B, C
Q: 2
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to use Kismet as a wireless sniffer to sniff the We-are-secure network. Which of the following IEEE-based traffic can be sniffed with Kismet?
Each correct answer represents a complete solution. Choose all that apply.
A. 802.11g
B. 802.11a
C. 802.11b
D. 802.11n
Answer: A, B, C, D
Q: 3
Which of the following processes is NOT a part of the Project Procurement Management Knowledge Area?
A. Develop Project Management Plan
B. Request Seller Responses
C. Contract Administration
D. Plan Purchases and Acquisitions
Answer: A
Q: 4
You work in an enterprise as a Network Engineer. Your enterprise has a secure internal network. You want to apply an additional network packet filtering device that is intermediate to your enterprise's internal network and the outer network (internet). Which of the following network zones will you create to accomplish this task?
A. Border network area
B. Autonomous system area (AS)
C. Demilitarized zone (DMZ)
D. Site network area
Answer: A
Honeypot Tutorial
Q: 5
Which of the following are countermeasures to prevent unauthorized database access attacks?
Each correct answer represents a complete solution. Choose all that apply.
A. Session encryption
B. Removing all stored procedures
C. Input sanitization
D. Applying strong firewall rules
Answer: A, B, C, D
Q: 6
Which of the following protocols does IPsec use to perform various security functions in the network?
Each correct answer represents a complete solution. Choose all that apply.
A. Internet Key Exchange
B. Encapsulating Security Payload
C. Authentication Header
D. Skinny Client Control Protocol
Answer: A, B, C
Q: 7
You are the project manager of a Web development project. You want to get information about your competitors by hacking into their computers. You and the project team determine should the hacking attack not be performed anonymously, you will be traced. Hence, you hire a professional hacker to work on the project. This is an example of what type of risk response?
A. Acceptance
B. Transference
C. Mitigation
D. Avoidance
Answer: B
Q: 8
You work as a project manager for BlueWell Inc. You are working with your team members on the risk responses in the project. Which risk response will likely cause a project to use the procurement processes?
A. Mitigation
B. Acceptance
C. Exploiting
D. Sharing
Answer: D
Q: 9
Which of the following statements is true about the difference between worms and Trojan horses?
A. Trojan horses are a form of malicious codes while worms are not.
B. Trojan horses are harmful to computers while worms are not.
C. Worms replicate themselves while Trojan horses do not.
D. Worms can be distributed through emails while Trojan horses cannot.
Answer: C
Q: 10
Victor wants to use Wireless Zero Configuration (WZC) to establish a wireless network connection using his computer running on Windows XP operating system. Which of the following are the most likely threats to his computer?
Each correct answer represents a complete solution. Choose two.
A. Attacker can use the Ping Flood DoS attack if WZC is used.
B. Information of probing for networks can be viewed using a wireless analyzer and may be used to gain access.
C. Attacker by creating a fake wireless network with high power antenna cause Victor's computer to associate with his network to gain access.
D. It will not allow the configuration of encryption and MAC filtering. Sending information is not secure on wireless network.
Answer: B, C
Q: 11
Which of the following cryptographic system services ensures that information will not be disclosed to any unauthorized person on a local network?
A. Authentication
B. Integrity
C. Non-repudiation
D. Confidentiality
Answer: D
Q: 12
You are the program manager of the JNH Program. Tom, a project manager in your program, has just completed his project and is ready to officially close his project. You agree that Tom's project is completed. What role do you play in Tom's project closure?
A. You must ensure that that the projects within the program have been closed at the project level.
B. You must ensure that the project sponsor closes the project.
C. You must ensure that the program management team closes the project for the project manager.
D. You must close the project before operations closes the project.
Answer: A
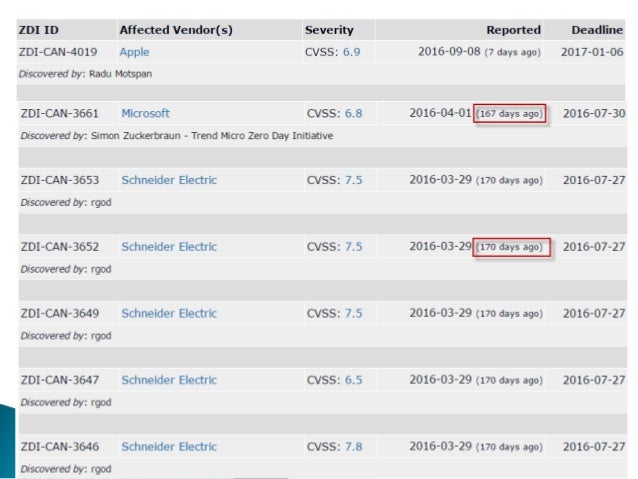
Q: 13
Which of the following types of attacks entices a user to disclose personal information such as social security number, bank account details, or credit card number?
A. Spoofing
B. Phishing
C. Password guessing attack
D. Replay attack
Answer: B
Q: 14
Which of the following are considered Bluetooth security violations?
Each correct answer represents a complete solution. Choose two.
A. Bluebug attack
B. Bluesnarfing
C. SQL injection attack
D. Social engineering
E. Cross site scripting attack
Answer: A, B
Q: 15
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
A. Linguistic steganography
B. Text Semagrams
C. Technical steganography
D. Perceptual masking
Answer: A, B
Q: 16
A helpdesk technician received a phone call from an administrator at a remote branch office.
The administrator claimed to have forgotten the password for the root account on UNIX servers and asked for it. Although the technician didn't know any administrator at the branch office, the guy sounded really friendly and since he knew the root password himself, he supplied the caller with the password.
What type of attack has just occurred?
A. Replay attack
B. Social Engineering attack
C. Brute Force attack
D. War dialing attack
Answer: B
Q: 17
Which of the following intrusion detection systems (IDS) monitors network traffic and compares it against an established baseline?
A. File-based
B. Anomaly-based
C. Signature-based
D. Network-based
Answer: B
Q: 18
A project team member has just identified a new project risk. The risk event is determined to have significant impact but a low probability in the project. Should the risk event happen it'll cause the project to be delayed by three weeks, which will cause new risk in the project. What should the project manager do with the risk event?
A. Add the identified risk to the issues log.
B. Add the identified risk to a quality control management control chart.
C. Add the identified risk to the low-level risk watchlist.
D. Add the identified risk to the risk register.
Answer: D
Q: 19
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. You install access points for enabling a wireless network. The sales team members and the managers in the company will be using laptops to connect to the LAN through wireless connections. Therefore, you install WLAN network interface adapters on their laptops. However, you want to restrict the sales team members and managers from communicating directly to each other. Instead, they should communicate through the access points on the network. Which of the following topologies will you use to accomplish the task?
A. Infrastructure
B. Star
C. Ad hoc
D. Mesh
Answer: A
Q: 20
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
A. Single Loss Expectancy (SLE)
B. Exposure Factor (EF)
C. Annualized Rate of Occurrence (ARO)
D. Safeguard
Answer: C
Q: 21
Which of the following terms describes the statement given below?
'It provides the testers with complete knowledge of the infrastructure to be tested, often including network diagrams, source code, and IP addressing information.'
A. BackTrack
B. GFI LANguard
C. White box penetration testing
D. Black box penetration testing
Answer: C
Q: 22
Which of the following is used to allow or deny access to network resources?
A. NFS
B. System hardening
C. ACL
D. Spoofing
Answer: C

Q: 23
Which of the following can be used as a countermeasure against the SQL injection attack?
Each correct answer represents a complete solution. Choose two.
A. mysql_escape_string()
B. session_regenerate_id()
C. mysql_real_escape_string()
D. Prepared statement
Answer: C, D
Q: 24
Which of the following penetration testing phases involves reconnaissance or data gathering?
A. Attack phase
B. Post-attack phase
C. Pre-attack phase
D. Out-attack phase
Answer: C
Q: 25
Which of the following statements are true about an application-level gateway?
Each correct answer represents a complete solution. Choose all that apply.
A. It allows client applications to use dynamic ephemeral TCP/UDP ports to communicate with the known ports used by the server applications.
B. It does not allow customized NAT traversal filters to be plugged into the gateway to support address and port translation for certain application protocols.
C. It is a security component that is added to a firewall or NAT employed in a computer network.
D. It converts the network layer address information found inside an application payload. The hosts can be on either side of the firewall/NAT.
Answer: A, C, D
Q: 26
Which of the following work as traffic monitoring tools in the Linux operating system?
Each correct answer represents a complete solution. Choose two.
A. IPTraf
B. Hotspotter
C. Ntop
D. John the Ripper
Answer: A, C
Q: 27
You work as a Network Administrator for McNeil Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company's management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks:
l The wireless network communication should be secured.
l The laptop users should be able to use smart cards for getting authenticated.
In order to accomplish the tasks, you take the following steps:
l Configure 802.1x and WEP for the wireless connections.
l Configure the PEAP-MS-CHAP v2 protocol for authentication.
What will happen after you have taken these steps?
A. The laptop users will be able to use smart cards for getting authenticated.
B. None of the tasks will be accomplished.
C. Both tasks will be accomplished.
D. The wireless network communication will be secured.
Answer: D
Q: 28
Which of the following are the tools and techniques of the Plan Procurements process?
Each correct answer represents a complete solution. Choose all that apply.
A. Contract types
B. Expert judgment
C. Probability and impact matrix
D. Make-or-buy analysis
Answer: A, B, D
Q: 29
Mark works as a Network Administrator for NetTech Inc. Several employees of the company work from the remote locations. The company provides a dial-up connection to employees to connect to the company's network using remote access service. Mark wants to implement call back feature for the employees who are dialing for long distance. Which of the following protocols will he use for remote access services to accomplish the task?
A. SLIP
B. WEP
C. UDP
D. PPP
Answer: D
Q: 30
You work as a project manager for an IT project. You are analyzing activity sequences, durations, resource requirements, and schedule constraints to create the project schedule. In which of the following Knowledge Areas are you working on?
A. Project Integration Management
B. Project Time Management
C. Project Scope Management
D. Project Risk Management
Answer: B